- By Tom Blok

Hacked? Don’t Know How? It might be caused by Credential Stuffing ..
Also known as: Credential Testing, Account Takeover, Brute Force Attack, Password Checking, Account Hijacking and Password List Attack.
We regularly see complaints about accounts that have been hacked. This is certainly not always the companies negligence. In fact, 'the hack' is often made possible by the carelessness of ourselves. Passwords are not always secret anymore, no matter how complex they are.
Table of Contents
What is Credential Stuffing?
Credential stuffing has become a serious problem over the years. In 2012 for example, hackers breached LinkedIn and dropbox. This caused a massive spike in credential stuffing victims. But what exactly is it, and how does it work?
Credential stuffing is a an automated process of stealing credentials through a data breach to gain access to other online accounts of a person. Through the years, fraudsters have gained billions of credentials as a result of data breaches.
After a data breach, the stolen information is misused on for instance:
- e-Commerce websites
- Online banking
- Streaming services
- Social Media
- Online gaming
On Complain.biz we have seen hundreds of these cases. Every widely known company with an online presence has been a victim of credential stuffing in the past years.
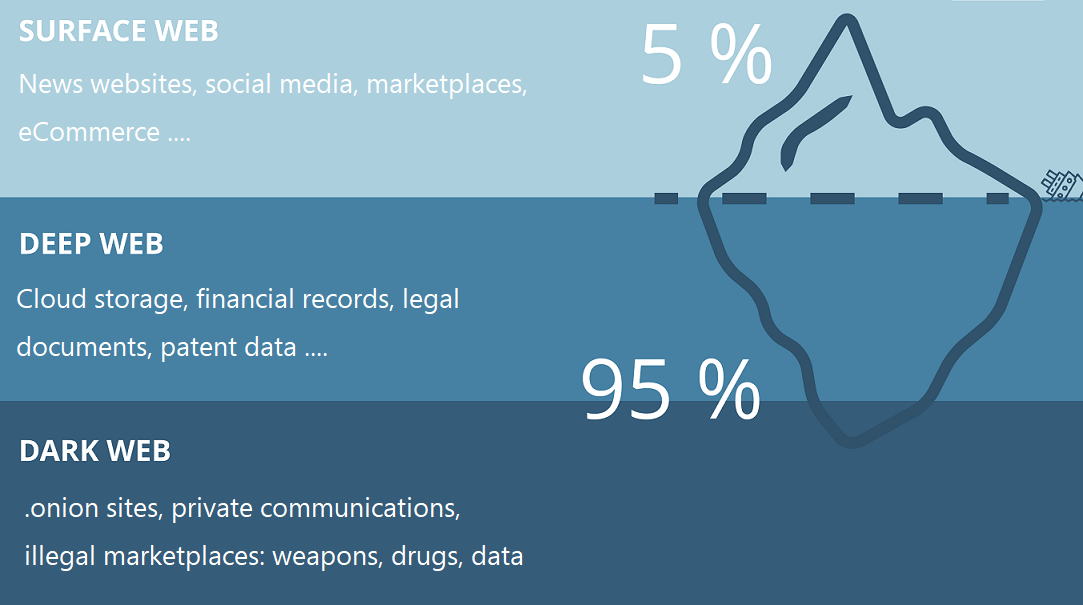
There is a pretty big underground economy facilitating credential stuffing. It can be found on the dark web where databases of peoples personally identifiable information such as: full name, date of birth, bank account number, email address, passwords etc. are being sold.
What is a Data Breach?
A data breach is an incident where information is stolen or taken from a database without the knowledge or authorization of the database’s owner.
When it’s on purpose (Black Hat), the hackers will extract all data from the database to be able to sell a list of usernames and passwords on the dark web. All your private data, credentials, and other sensitive information are at risk and prone to falling into the wrong hands.
Do you want to know if your credentials have fallen victim to such an incident? You can check it yourself on Have I Been Pwned. HIBP is a website that tracks over 8.5 billion compromised credentials from over 410 data beaches. It helps you check if your personal data has been compromised in a (known) data breach.
Role of Passwords
You have been facing all the security complexity, checking boxes to prove you’re not a bot, and making passwords longer because of the extra security measures the websites are taking.
Unfortunately many people have a habit by choosing a few typical passwords that fit the passwords’ criteria with upper case, lower case, and numbers. Then, we reuse the same passwords for all our accounts across the web.
This is where we make it easier for hackers to abuse our accounts. They extract the database of one website, and suddently they have the password to all your accounts on the web.
How does credential stuffing work?
We all have heard about hacked accounts on websites like Amazon, AliExpress and Wish. When hackers break into someone’s account, they change the email, purchase items, and use the victim’s credit card to pay. Credential Stuffing is the answer on how they manage to gain acces.
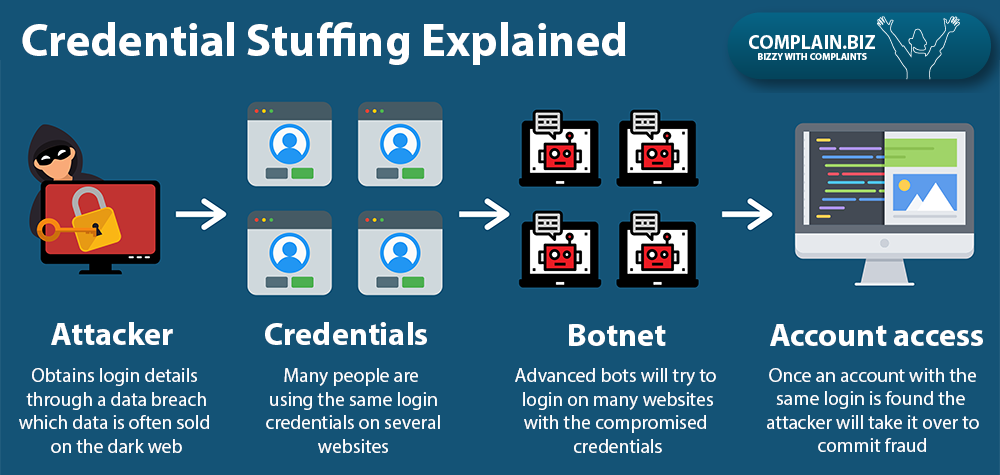
Credential stuffing explained:
- The attacker / hacker obtains login details through a data breach
- Many people are using the same login credentials on several online services
- Advanced bots use the compromised credentials trying to login on many websites
- Once an account with the same login is found they will take it over to commit fraud
Statistics show that approximately 0.1% of the breached credential logins into another service are likely to be successful.
Now the worst part.. even if a password does not work for an account, it is not very difficult for them to reset it. Due to the massive amount of personal information they gained, it is easy to trick customer service agents for account recovery.
How Big is the Problem?
It is huge! From 2017 to 2019, Akamai, a content delivery network (CDN), detected 55 billion credential stuffing attacks. Akamai found that attackers most often targeted retail sites, video-streaming services, and entertainment companies.
Here are some cases reported on our website where we suspect credential stuffing:
How to protect yourself against credential stuffing?
Frankly, credential stuffing is challenging to defeat. Online services don’t always have a foolproof way of defending their database. Data leaks will keep happening. And hackers will try take advance from it.
The main weakness is that someone is using the same password across multiple online services. Even the most complicated string of characters can not protect your account. This doesn’t mean you have to compromise all your other accounts though.
The best way to protect your account from credential stuffing is by using different passwords for each of your online accounts. A password manager (often built in your browser) can help you with that.
Additionally, use two-factor authentication wherever you can. We also advise to change your passwords once in a while. Again, there are many password managing tools to help you with all this.
To sum up:
- Use different passwords and a password manager
- Use two-factor authentication wherever you can
- Change your passwords once in a while
Final (obvious) advice: If someone gained access to one of your online accounts, change all your passwords right away!
File your complaint on Complain.biz. We will give your complaint the attention it deserves.